c1337Shell
By Narcissus
The link leads to a fancy looking site with input and output boxes:
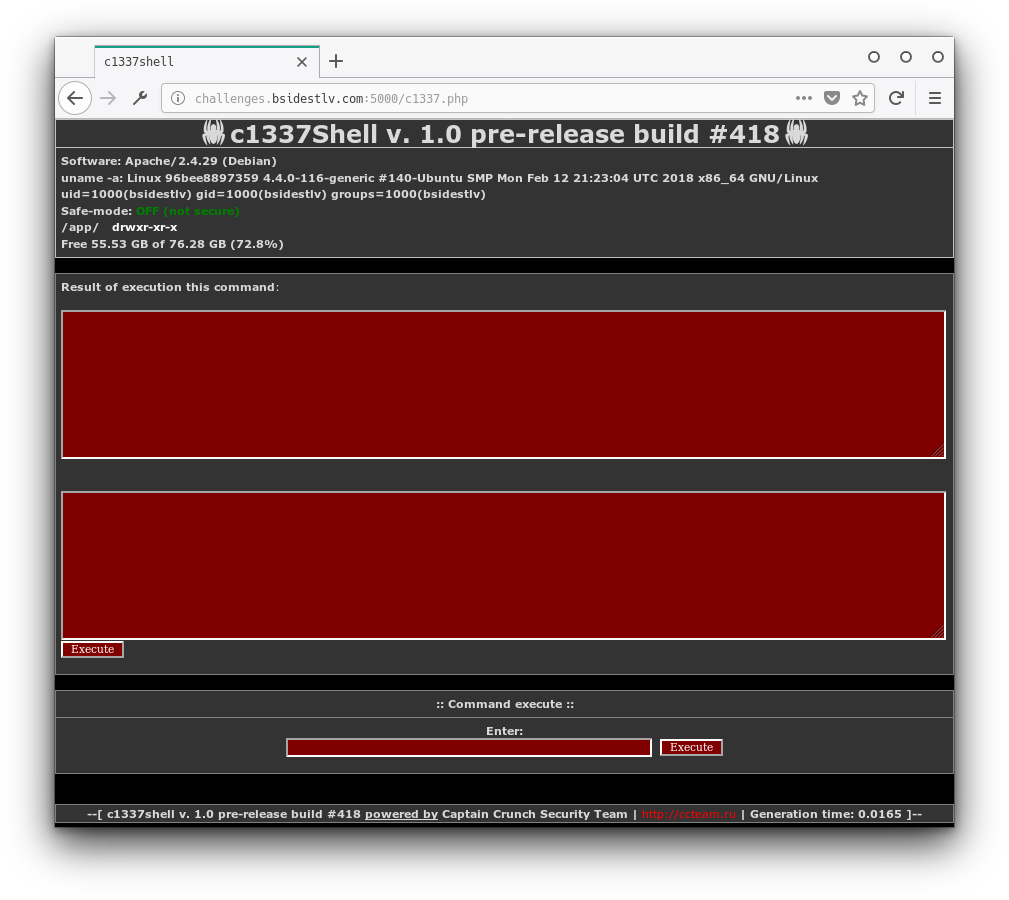
So we tried classic commands like ls and cd, but we kept getting the following error: error: bad characters found.
We then started trying wild-cards. * gave us nothing, but /* returned /app /bin /boot /dev /etc /home /lib /lib64 /media /mnt /opt /proc /root /run /sbin /srv /sys /tmp /usr /var. That means we are probably on the right track.
In the details area at the top of the site we see it says /app/, let's see if there is anything in there. Running /???/* returns lots of results, most importantly /app/f.
Let's check inside that: /???/?/* gives us /app/f/fl.
Another few levels in: /???/?/*/*/* returns /app/f/fl/flag/flag_is_here /app/f/fl/flag/flag_is_not_here.
Apparently we need to get into the folder that says it has the flag running /???/?/*/*/????_??_????/* returns /app/f/fl/flag/flag_is_here/flag.txt great! Now we need to read this file somehow.
So far we've come to understand that the system takes our input, makes sure there are no letters/numbers in it and runs it through echo or similar. We'll guess echo.
If we were to input /???/??? /???/?/*/*/????_??_????/* we would get:
/bin/cat /bin/dir /bin/pwd /bin/sed /bin/tar /dev/pts /dev/shm /dev/tty /etc/X11 /etc/apt /etc/gss /etc/opt /etc/rmt /etc/rpc /etc/ssl /etc/xdg /etc/xml /lib/cpp /lib/lsb /sys/bus /sys/dev /usr/bin /usr/lib /usr/src /var/lib /var/log /var/opt /var/run /var/tmp /app/f/fl/flag/flag_is_here/flag.txtTo run a program using echo we can surround the program's name with backticks.
As we can see /bin/cat is the first program in the list, therefore it will run, and get all the other programs and flag.txt as its input.
So we wrapped the command with backticks got lots of "garbage" but at the very end we also got the flag: BSidesTLV{1_l1k3_wildcards_&_r3g3x_but_h8_th3_cr34t0r}
(The shortest input I found is /*/??? /*/?/*/*/*_??_????/*)

