Back To The 90s
- Category: Reversing
- 400 points
- Solved by JCTF Team
Description
Solution

For this challenge, we get the URL of a good old snake game. Really back to the 90's. First, let's play a little. The game consists of controlling a never-stopping snake to catch "fruits" (made of a few pixels each) without crashing in the walls or on itself. There are two types of fruits. The ^ and the x. After a few games, it was clear than even if their position was looking random, their order was not. It always started:
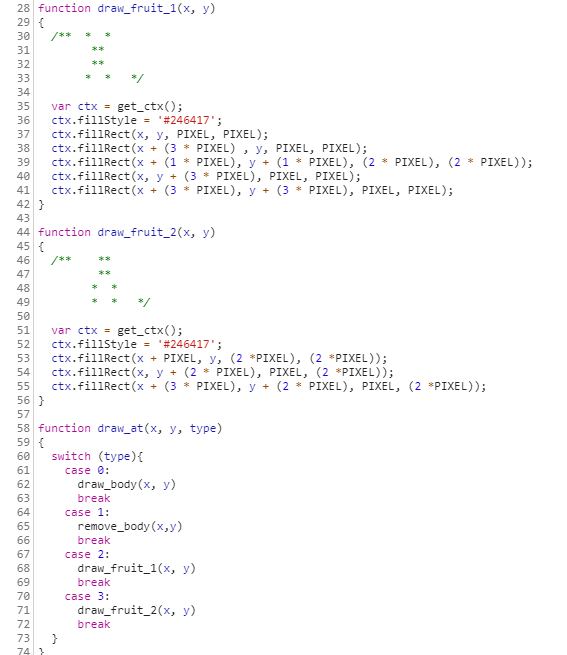
^x^^^^x...It was important, and we suspected it could already be the flag encoded as 0's and 1's, but we didn't want to play the game and exfiltrate the flag "bit by bit", so we just took another way to solve it :-) Looking at the source, there was very little "readable code". In a JavaScript file, snake.js, we found the different types of drawing of the game, including the 2 fruit types:
But all the logic came from a wasm file (snake.wasm). Wasm is the abbreviation of "WebAssembly", and is a portable binary code format, that can be compiled from high level languages (like C++, Rust, ...) to run natively in the same sandbox as JavaScript. It can also directly be disassembled (to an intermediate representation) and debugged from the development tools found in browsers like Firefox or Chrome.
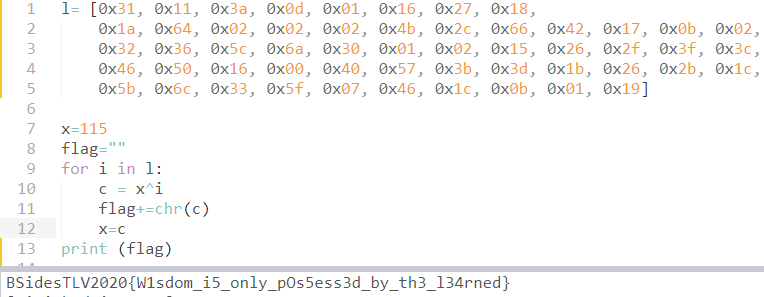
At the end of the wasm file was a huge array of 0's. Except 54 bytes, at the exact offset 1024.
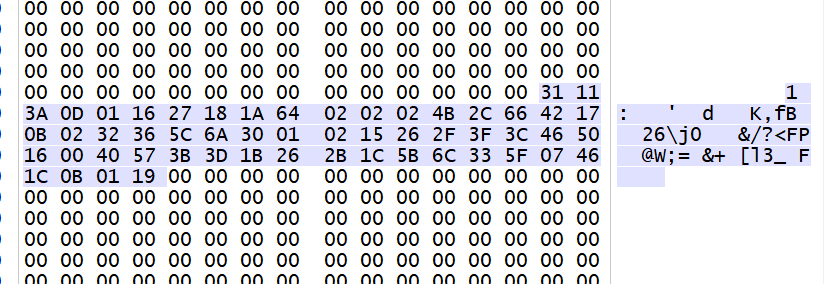
Looking for an access to this offset within the disassembled code, we find one place, and incidentally, it is xor-ed just a few instructions after.

So we put a break-point on these lines, and let's see what we get.
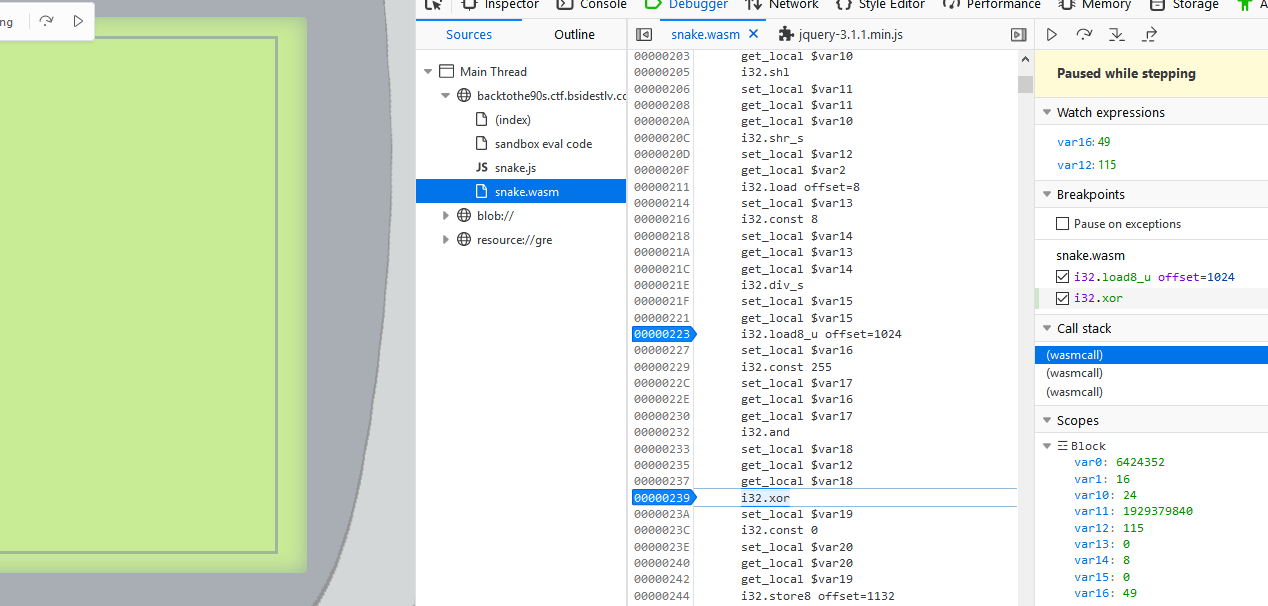
We see the first byte of the array (49 = 0x31) xor-ed with some value 115, coming from offset 1132. And immediately after, the result of the xor is stored at offset 1132. At this stage, it's already clear that if go back this path, we'll xor the next byte with the result of the previous xor.
So we just wrote the following few lines and got the flag.