1337RFCs
- Category: Dev
- 250 points
- Solved by JCTF Team
Solution
This challenge presented a pdf, and the description hinted that something was hidden in it. The pdf itself presented a dummy plain text RFC converted to pdf. The file itself was 66.5 KB. Was it Forensics? Stegano? It's in the RE category after all...
Well, this part was not difficult to find. First, there is a huge hint at the end of the pdf:
this RFC is so boring... I would give it the BOOT
And the "file" utility returns: $ file rfc1337.pdf rfc1337.pdf: DOS/MBR boot sector
A pdf file that is also bootable image? Polyglot! Luckily, I have next to me my beloved collection of PoC||GTFO. This one looked very much like the one presented in PoC||GTFO 0x02, a.k.a. Children’s Bible Coloring Book of PoC||GTFO.
 "This OS is also a PDF", with the original colored pencils
"This OS is also a PDF", with the original colored pencils
It gives directly the right command line to run it: qemu-system-i386 -fda pocorgtfo02.pdf rfc1337.pdf
(Forgetting the -fda option returns a message indicating that the file should be booted as a floppy disk)
Now, we have several plans: trying to statically analyze the file; dumping the process; debugging it. I tried the second option, and dumped the memory of the qemu process, and searched for the INTENT{...} flag. Since I didn't find the flag, I moved to the 3rd option. Too bad I didn't continue a little more looking at the dump, since the Password (and not the flag) was easy to identify, and the writeup would have been shorter. But well, it would have been also a little boring, so let's look at the positive side and debug it.
First, I tried to debug it with qemu, that has an integrated gdb server, but for some reason, the memory I got there was not really workable. So I quickly turned to IDA+Bochs Debugger.
Following these instructions to create the Bochs Disk Image, the config file, and creating a 1.44 MB floppy disk with the pdf embedded as its start, we got the setup in place.
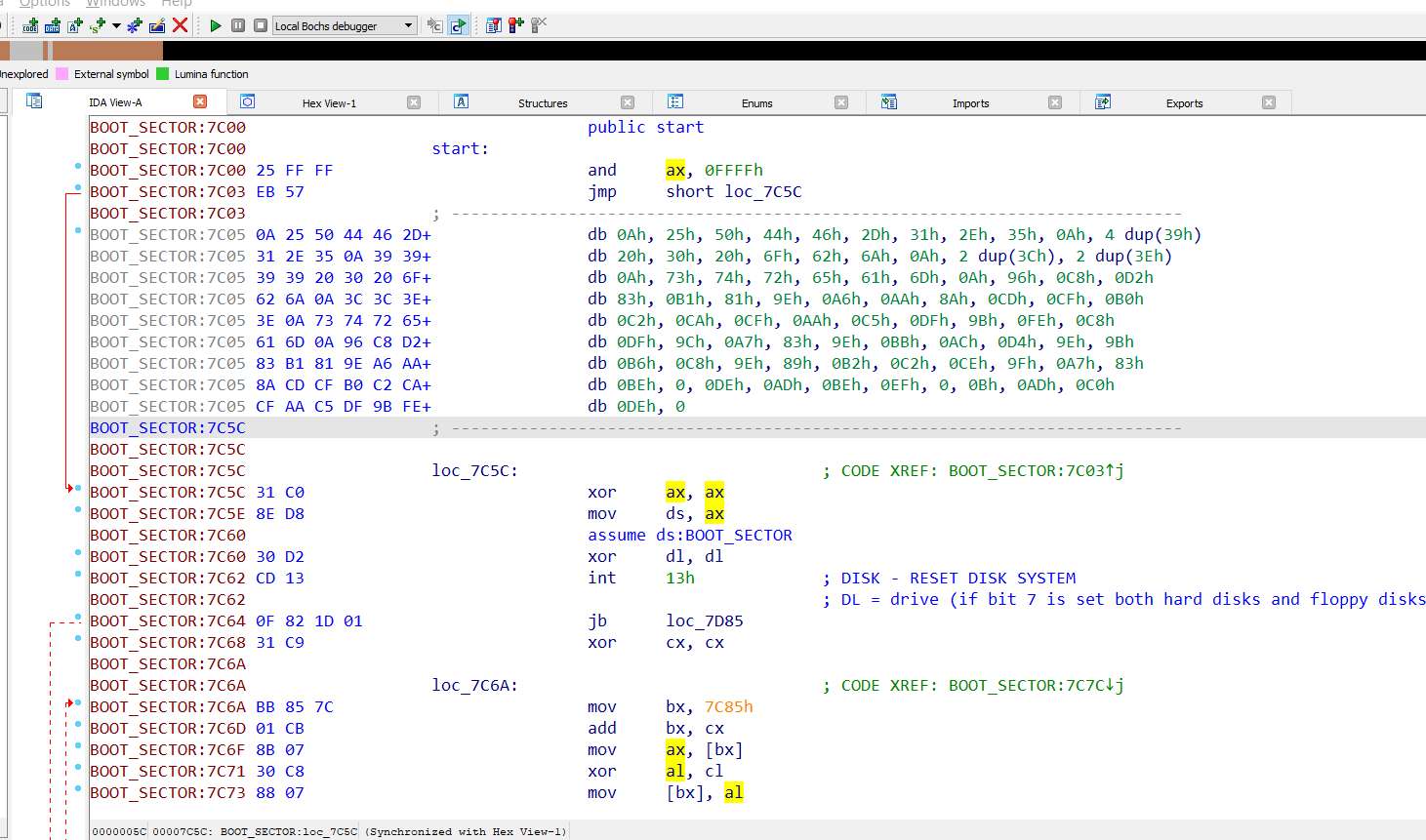
At the beginning of the boot sector, we have several "decryption loops" at the beginning, and a few checks (for example, that we're running from a floppy disk).
Instead of following all the flow and after we understand that the code is pushed in the next section ("debug002:7E00" in IDA), we put a HW breakpoint at the beginning of this section (hoping that the code after the boot sector will start from the there).
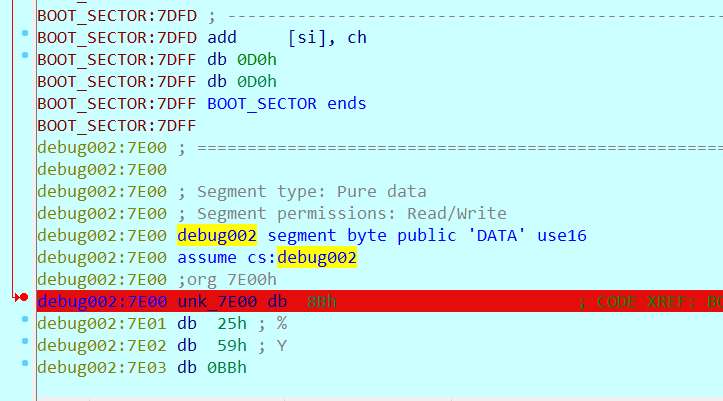
And luckily, after continuing the execution, we hit the breakpoint, with the decrypted code.
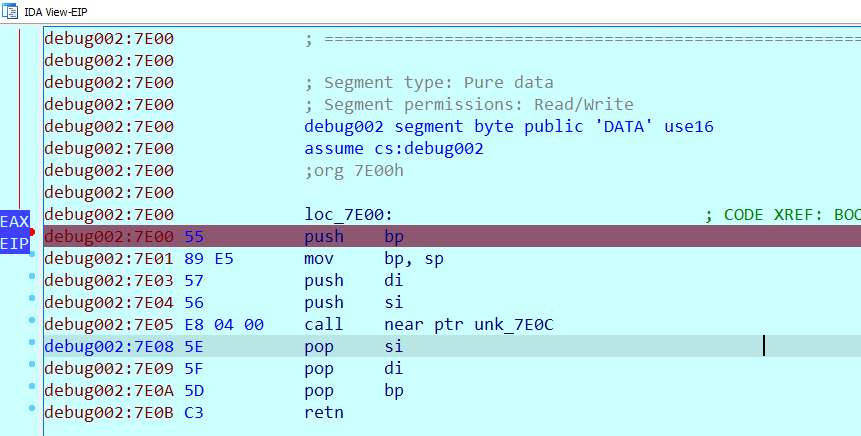
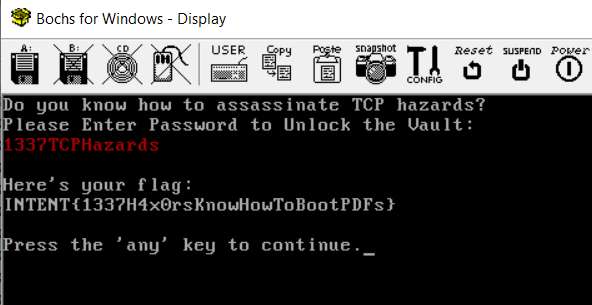
The critical function is found at 81B0. This function gets the input, and checks it. Early on, the address 7C00 is used for several things, like comparing the length of zero-terminated string at this address to the length of the input, and later, to compare its content.
The which is "1337TCPHazards". Entering this password in the emulator reveals the flag. (Following the decrypting procedure was not so complicated, but would have taken more time...).