Digging Session
- Category: Forensics
- 50 Points
- Solved by the JCTF Team
Description
Solution
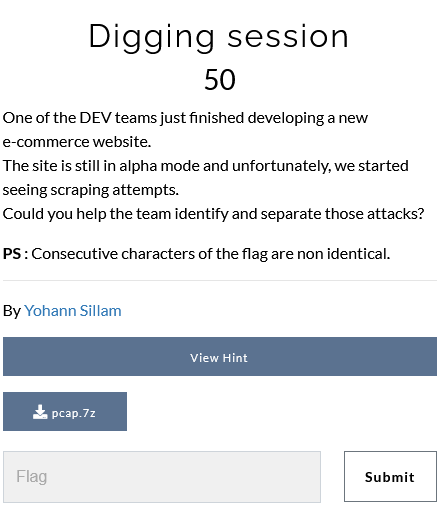
After looking inside the supplied PCAP file, we've got no clue about the desired flag. The PCAP file contains 26 TCP sessions. After using the hint, we've noticed that each packet's HTTP header contains a decimal value after the word "Chrome", under User-Agent field.
We exported all 26 sessions into files, then we used the following BASH command to export the values into their ASCII representation:
for j in {0..25}; do for i in `cat s$j.txt | grep Chrome/ | cut -d " " -f11 | grep Chrome | cut -d "/" -f2`; do printf "\x$(printf %x $i)"; done; echo; doneThe output:
LLLLLiiieiaaasocnv ddoo iiss mmaakke
LLLLiiffee iiiss aaasoooiicccceess aan
LLLLLLieee iasv ccaann
LLLLLLLasseerriiieessnvvveerryytthhiinngg wwee
LLLLLLasonnndd eev
LLLLLss offf cchhho
LLLLLLLe iaaa ssseerriiiees aedmIIINNTTEENNTT{{AA4
LLLLLs edddoo iisss m
LLLLLeeee iiiisss aasss ooff dmI4t
LLLLLs aeeevveerryytthhiinngg wwee ccaann d
LLLLiiiees aaanndd e
LLLLLLLs cchhhooiiicceess a
ehIE{{{AA44t
ehIIINNTTE
eee tth
mmmaakkee tthheemm.. I
hhheemm.. I
IE{t3l
EEENNTT{
{t333__DD3344aa11l
I4tttii00nn__4400__ttHH33__DD3344aa11ll55}}
ttt33nnttii00nn__4400__ttHH3
444tt33nnt
t
3l
lll55}}We noticed some interesting lines, that remind us a flag format:
LLLLLLLe iaaa ssseerriiiees aedmIIINNTTEENNTT{{AA4
ehIE{{{AA44t
ttt33nnttii00nn__4400__ttHH3
I4tttii00nn__4400__ttHH33__DD3344aa11ll55}}If we remove the irrelevant parts and concatenate those line by their common parts, we get:
IIINNTTEENNTT{{AA44ttt33nnttii00nn__4400__ttHH3__DD3344aa11ll55}}Using the following Python script, we removed duplicated consecutive characters:
#!/usr/bin/python3
t = "IIINNTTEENNTT{{AA44ttt33nnttii00nn__4400__ttHH3__DD3344aa11ll55}}"
res = ""
for i in range(1, len(t) - 1):
if t[i] == t[i + 1] and i != len(t) - 2:
continue
res += t[i]
print(res)And there it is:
INTENT{A4t3nti0n_40_tH3_D34a1l5}